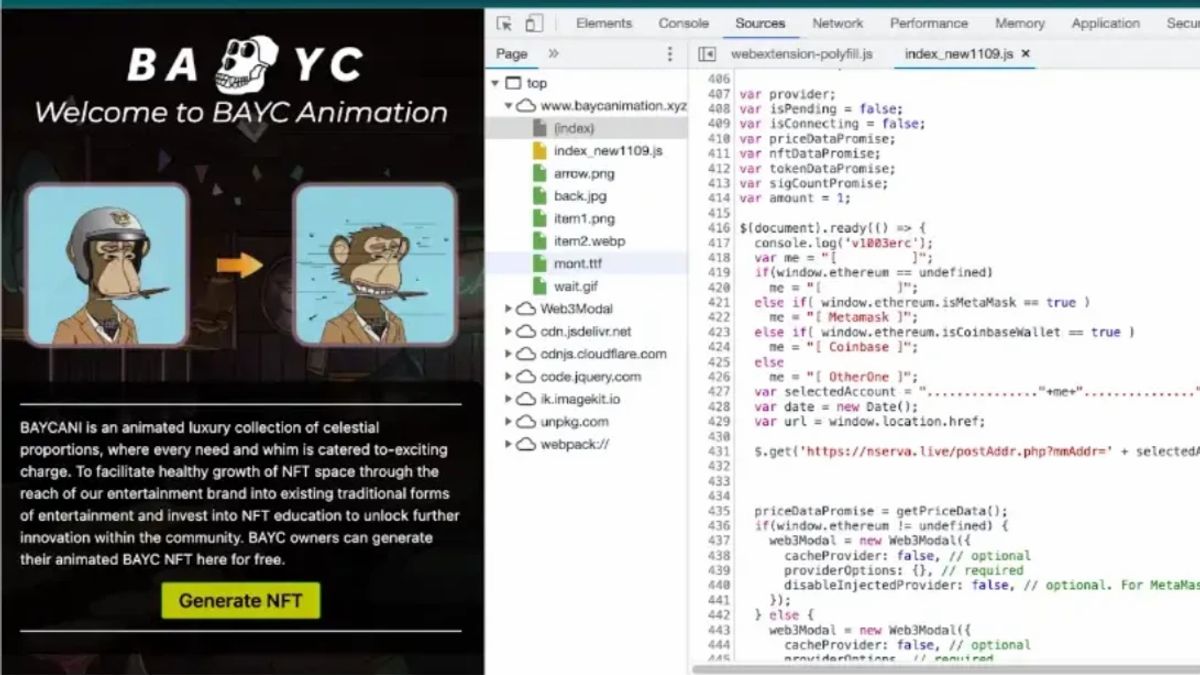
JAKARTA - Hackers associated with North Korea's Lazarus Group are reportedly behind a massive phishing campaign targeting non-fungible token (NFT) investors by leveraging nearly 500 phishing domains to deceive victims.
Blockchain security firm SlowMist released a report on December 24, which revealed the tactics North Korea's Advanced Persistent Threat (APT) group used to separate NFT investors from their NFTs. This includes using bait sites disguised as various NFT-related platforms and projects.
Examples of these fake websites include sites that pretend to be projects related to the World Cup, as well as sites that impersonate well-known NFT marketplaces such as OpenSea, X2Y2, and Rarible.
🚨SlowMist Security Alert🚨
North Korean APT group targeting NFT users with large-scale phishing campaign
This is just the tip of the iceberg. Our thread only covers a fraction of what we've discovered.
Let's dive in pic.twitter.com/DeHq1TTrrN
— SlowMist (@SlowMist_Team) December 24, 2022
SlowMist says one tactic used is to have these decoy sites offer "malicious Mints", which involves trying to trick victims into thinking they are printing out legitimate NFTs by connecting their wallets to the website.
However, the NFT is actually fraudulent, and the victim's wallet is left vulnerable to hackers who now have access to it.
The report also revealed that many phishing websites operate under the same Internet Protocol (IP), with 372 NFT phishing websites under one IP and another 320 NFT phishing websites linked to another IP.
SlowMist says the phishing campaign has been going on for several months, and notes that the earliest registered domain names appeared about seven months ago.
Other phishing tactics used include recording visitor data and saving it to external sites and linking images to the target project.
Once the hacker wants to get the visitor data, they will then proceed to run various attack scripts on the victim, which will allow the hacker to access the victim's access records, authorization and usage of the plug-in wallet, as well as sensitive data. such as victim consent records and sigData.
SEE ALSO:
All of this information then allows the hacker to access the victim's wallet, exposing all of their digital assets.
However, SlowMist emphasizes that this is only the "tip of the iceberg", as this analysis only looks at a fraction of the material and extracts "some" of the phishing characteristics of North Korean hackers.
For example, SlowMist highlights that just one phishing address can earn 1.055 NFT and generate 300 Ether worth 367.000 (IDR 5.7 billion), through phishing tactics.
It added that the same North Korean APT group was also responsible for the Naver phishing campaign previously documented by Prevailion on March 15.
North Korea is accused of becoming the center of various cryptocurrency theft crimes in 2022.
According to a news report published by South Korea's National Intelligence Service (NIS) on December 22, North Korea is suspected of stealing 620 million (IDR 9.6 trillion) worth of cryptocurrency this year alone.
In October, Japan's National Police Agency sent a warning to the country's crypto asset businesses to be wary of North Korean hacking groups.
The English, Chinese, Japanese, Arabic, and French versions are automatically generated by the AI. So there may still be inaccuracies in translating, please always see Indonesian as our main language. (system supported by DigitalSiber.id)