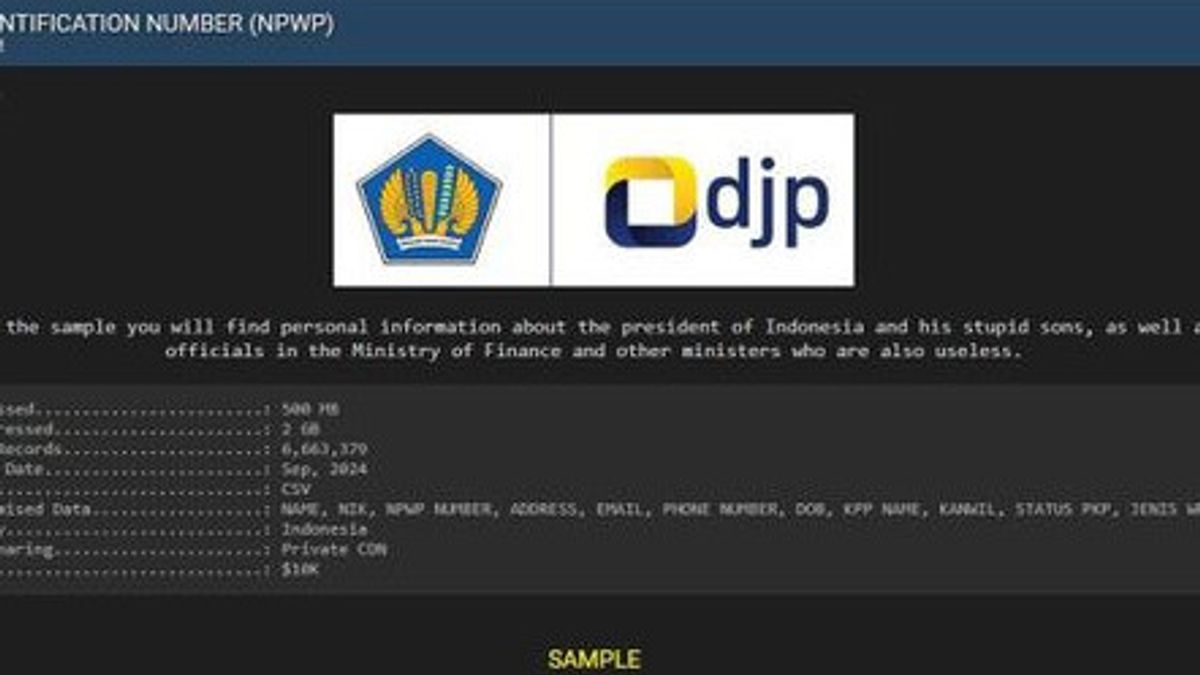
JAKARTA - Data leak incidents are still happening in Indonesia, the latest of which is the alleged leak of 6 million NPWP data. This incident then highlighted the urgency to strengthen cybersecurity measures in various institutions and organizations.
Seeing this incident, ITSEC Asia as a leading cybersecurity company in the Asia-Pacific region is responding to the need for evaluation and proactive measures to increase digital infrastructure protection in data management is important in order to maintain public trust.
"This alleged data leak serves as a reminder that all institutions that manage sensitive data must continue to update their security framework," said Joseph Lumban Gaol, President Director of PT ITSEC Asia Tbk in a written statement received on Sunday, September 22.
Joseph also emphasized the importance of implementing a comprehensive and complete Data Protection solution to minimize the risk of data leakage and the importance of collaboration between stakeholders in increasing critical infrastructure protection.
Furthermore, ITSEC Asia recommends several tactical steps that can be implemented in strengthening system security, protecting sensitive data, including:
Data And Security Storage Audit
Conducting important data storage point audits and security systems to evaluate security control on data. Security testing such as Penetration Testing is also needed for risk analysis and security loopholes.
Stricter User Access Restrictions
By adopting stricter access control policies, the number of individuals interacting with important information will be less, and reduce the risk of data exposure from internal parties or unauthorized parties.
Data Animization For Stronger Security Control
Agencies also need to implement a stronger data protection mechanism, such as anonymity carried out by removing or encrypting identification factors that connect individuals with stored data. Thus, exposed data cannot be easily used by criminals.
Strong Security Equipment With 24-7 Monitoring
To improve the ability to maintain data security, it is necessary to implement advanced analytic systems and real-time monitoring dashboards. Continuous monitoring of sensitive data activity is essential for real-time identification of suspicious access patterns or unauthorized access patterns.
Detailed Access Log Collection And Storage
By carefully recording who accessed sensitive data, when the data is accessed, and for what purpose, it will not only prevent suspicious access, but also ensure that such activity can be tracked clearly.
However, Joseph appreciated the ongoing efforts made by the relevant authorities in dealing with the alleged data leak quickly and transparently.
The English, Chinese, Japanese, Arabic, and French versions are automatically generated by the AI. So there may still be inaccuracies in translating, please always see Indonesian as our main language. (system supported by DigitalSiber.id)