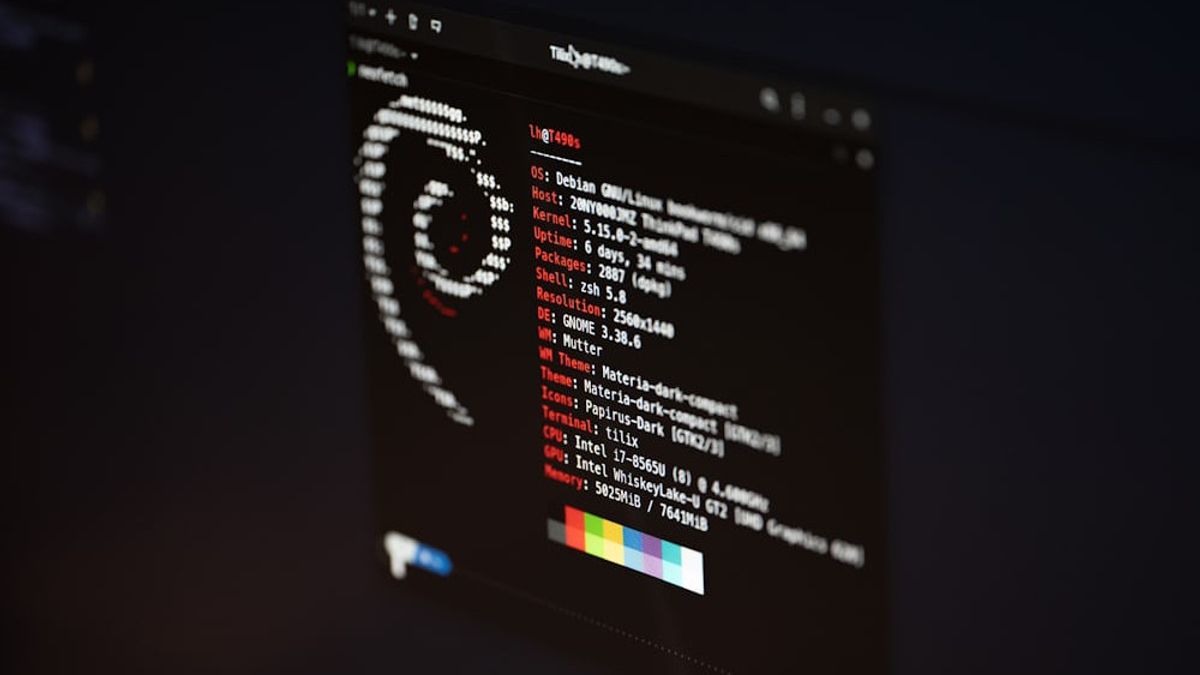
JAKARTA - Kaspersky has discovered a new backdoor variant of Dinodasrat targeting Linux, which has been actively infiltrating organizations in China, Taiwan, Turkey, and Uzbekistan since at least October 2023.
The global cybersecurity company said the variant could allow cybercriminals to monitor and control compromised systems secretly.
Furthermore, the findings of Kaspersky's Global Research and Analysis Team (GReAT) show where the Linux variant developed in C++ is designed to infiltrate the Linux infrastructure undetected.
Once infected, the malware will collect important information from the host machine to create a unique identifier (UID) without collecting user specific data, thus avoiding early detection.
Once contacts with the C2 server are intertwined, the implant stores all local information regarding the victim's ID, privileges, and other relevant details in a hidden file called "/etc/.netc.conf".
Kaspersky also found that this malware is programmed to automatically send data taken every two minutes and 10 hours.
All Kaspersky products detect this Linux variant as HEUR:Backdoor.Linux.Dinodas.a.
Thus, Kaspersky's latest findings highlight that even the well-known Linux security is not immune to threats.
SEE ALSO:
"This underscores the fact that cybercriminals continue to develop their tools to avoid detection and target more victims," added Leandro Ubiedo, security expert at GReAT (Global Research and Analysis Team) Kaspersky.
Kaspersky urged all members of the cybersecurity community to exchange knowledge about the latest findings to ensure business cybersecurity is maintained.
The English, Chinese, Japanese, Arabic, and French versions are automatically generated by the AI. So there may still be inaccuracies in translating, please always see Indonesian as our main language. (system supported by DigitalSiber.id)