JAKARTA - Microsoft discovered North Korean-sponsored hacker group Lazarus, using open-source software and creating fake jobs to spread malware through Linkedin.
Lazarus, also referred to as ZINC, flow Chollima, and Black Artemis, is a state-sponsored military hacker group from North Korea. They have been active since at least 2009, and have since been responsible for major attacks, including phishing, ransomware campaigns, and more.
In fact, they are involved in espionage, data theft, hacking of crypto exchanges and banking systems, even network destruction.
They are also well known for targeting many major industrial sectors, such as technology, media entertainment, aerospace, IT services in the United States (US), Britain, India, and Russia, and they used various types of software to carry out these attacks.
Microsoft Threat Intelligence Center (MSTIC) has seen the group use PuTTY, KiTTY, TightVNC, Sumatra PDF Reader, and software installer muPDF/Subliminal Recording for this attack since late April this year.
In the findings of MSTIC, Lazarus carried out spear-phishing in the technology and media sectors with a false job offer in July, using WhatsApp to share the example of trojan Putty.
"The Microsoft researchers have observed the spear-phishing as the main tactic of ZINC players, but they have also been observed using strategic website compromises and social engineering on social media to achieve their goals," wrote the MSTIC researcher.
"ZINC targets enterprise employees who are trying to be infiltrated and are trying to force these people to install seemingly harmless programs or open armed documents containing malicious macro. Targeted attacks have also been carried out on security researchers via Twitter and LinkedIn," he added.
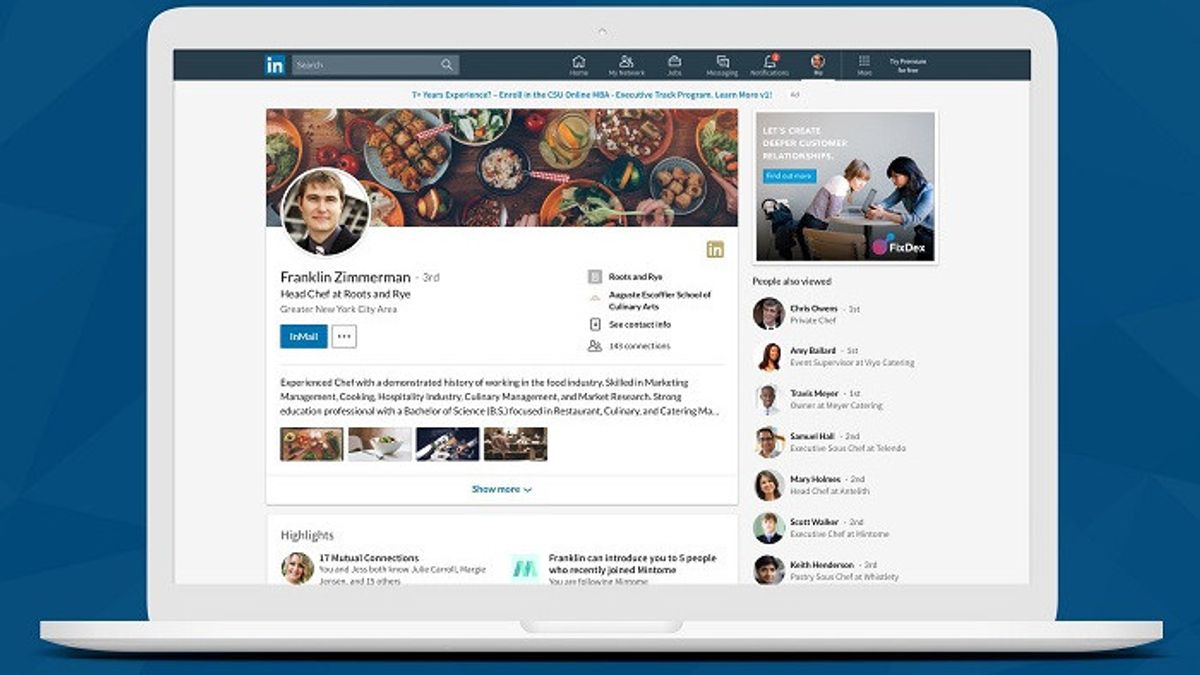
Launching Digital Trends, Monday, October 3, the security team on Microsoft's LinkedIn also saw these actors create fake profiles to disguise themselves as recruiters from companies in the technology, defense and media entertainment sector. Later if the victim is interested, they will be directed to WhatsApp to share the malware.
Google Threat Analysis Group (TAG) found drive also using Twitter, Discord, YouTube, Telegram, Keybase, and emails with similar tactics last January.
US authorities warn companies in the country and Europe to exercise caution against IT contractors who applied for support and the role of developers last year.
But now, the LinkedIn Threat Prevention and Defense team has stopped that fake account. Even so, Microsot asks users the next time they get a message on LinkedIn, they have to be careful.
The English, Chinese, Japanese, Arabic, and French versions are automatically generated by the AI. So there may still be inaccuracies in translating, please always see Indonesian as our main language. (system supported by DigitalSiber.id)