JAKARTA - A 24-year-old video game designer who runs his small business from a house next to an old Cypriot church on the outskirts of Nicosia is now entangled in a global crisis following Russia's invasion of Ukraine.
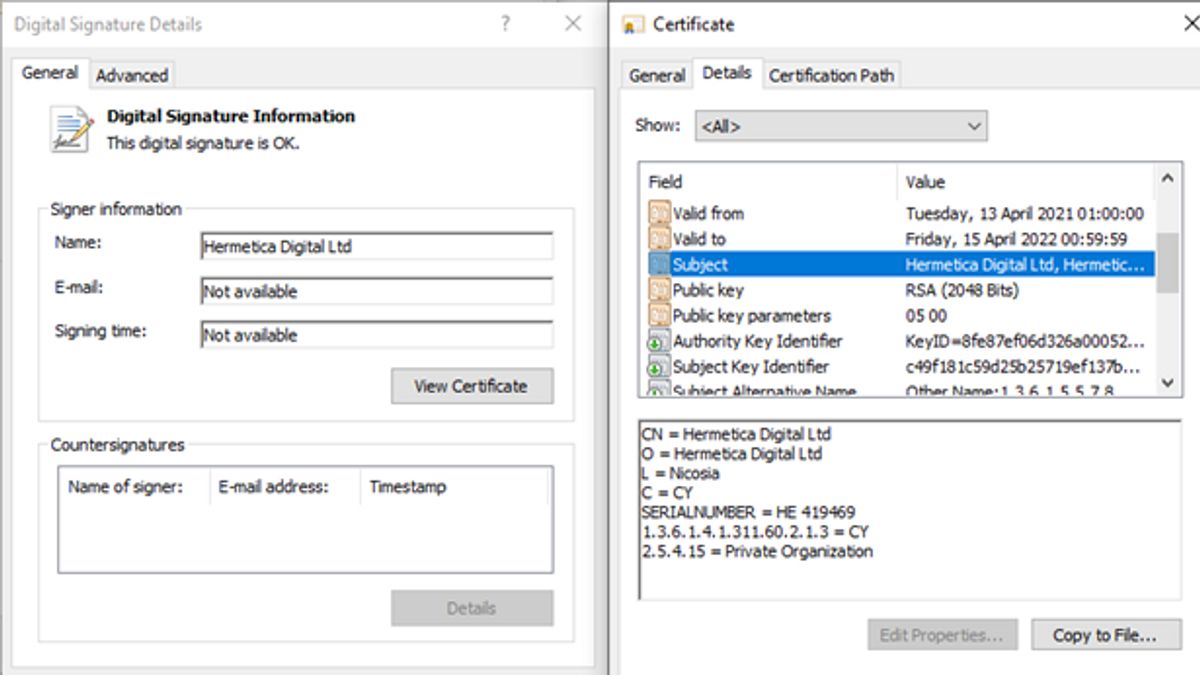
Trachonitis Police's company Hermetica Digital Ltd has been implicated by US researchers in a data-destroying cyberattack that hit hundreds of computers in Ukraine, Lithuania and Latvia.
Hermetica's digital signature, found in traces of a digital attack on Wednesday evening, February 23. It was just hours before Russian troops entered Ukraine, and the cyberattack was widely seen as a prelude to the Moscow invasion.
The malware was signed using a digital certificate with Hermetica Digital's name on it, according to the researchers. Some of them started calling the malicious code "HermeticWiper".
Trachonitis, the founder of Hermetica, told Reuters he had nothing to do with the attack. He said he had never asked for a digital certificate and had no idea that a certificate had been issued for his company.
He said his role in the video game industry was simply to write text for games that other people put together.
The Wiper binary is signed using a code signing certificate issued to Hermetica Digital Ltd 3/n pic.twitter.com/sGCl3Lbqc1
— ESET research (@ESETresearch) February 23, 2022
"I don't even write code - I write stories," he said. He also added that he was not aware of the connection between his company and the Russian invasion until he was alerted by a Reuters reporter on Thursday morning, February 24. "I'm just a Cypriot man ... I have no relations with Russia," he said.
The extent of the damage caused by the Hermetica malware attack was unclear, but cybersecurity firm ESET said malicious code had been found installed on "hundreds of machines".
Western leaders have warned for months that Russia could carry out a destructive cyberattack against Ukraine before the invasion.
Last week, Britain and the United States said Russian military hackers were behind a spate of denial of service (DDoS) attacks that briefly took Ukrainian banking and government sites offline.
Cyberspies routinely steal the identities of random strangers to rent server space or register malicious websites.
The Hermetica Digital certificate was issued in April 2021, but the timestamp on the malicious code itself is December 28, 2021.
ESET researchers said in a blog post that the dates suggest that "the attack may have been going on for some time."
If the attack was carried out by Russia, then the timing mark could potentially be a significant data point for observers hoping to understand when the planned invasion of Ukraine came together.
ESET's head of threat research, Jean-Ian Boutin, told Reuters that there were various ways in which bad actors could fraudulently obtain code signing certificates.
SEE ALSO:
"They can obviously get it themselves, but they can also buy it on the black market," Boutin said. "Thus, it is possible that the operation went further than we previously knew, but it is also possible that the threat actor obtained this code signing certificate recently, just for this campaign."
Ben Read, director of cyber espionage analysis at Mandiant, said it was possible that a group could "impersonate companies in their communications with digital certificate providers and obtain legitimate certificates that were fraudulently issued to them."
Cybersecurity firm Symantec said organizations in the financial, defense, aviation, and IT services sectors were targeted by attacks on Wednesday, February 23. DigiCert, the company that issues digital certificates, did not immediately respond to a request for comment.
Juan-Andres Guerrero-Saade, a cybersecurity researcher at digital security firm SentinelOne, said the purpose of the attack was very clear. "It is meant to damage, incapacitate, signal, and cause chaos," Guerrero-Saade said.
The English, Chinese, Japanese, Arabic, and French versions are automatically generated by the AI. So there may still be inaccuracies in translating, please always see Indonesian as our main language. (system supported by DigitalSiber.id)