JAKARTA - Two Russian nationals, Artur Sungatov and Ivan Kondratyev, were subjected to legal action by the United States (US) and Britain for allegedly being involved in a ransomware attack using LockBit, one of the most dangerous ransomware variants at this time.
The US Treasury Department's Department of Foreign Asset Control Office (OFAC) has designated ten crypto wallet addresses linked to the two suspects on a specifically appointed list of citizens. The addresses are allegedly used to receive ransom funds from LockBit victims.
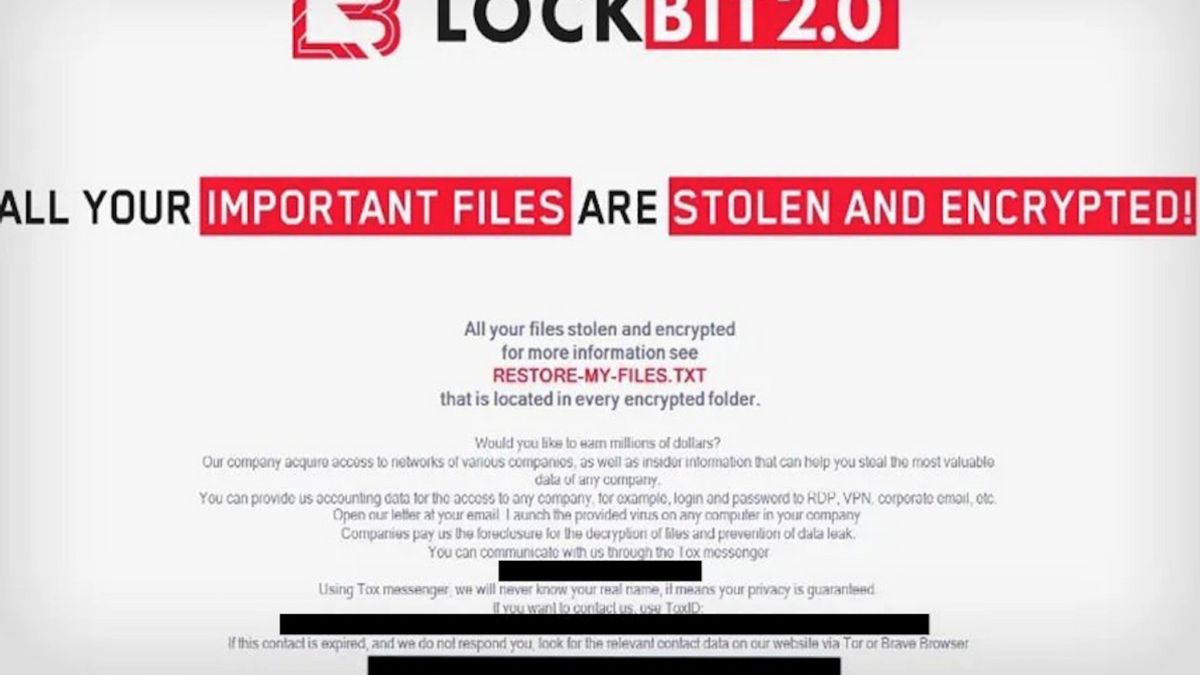
According to the US Department of Justice, LockBit is a Russian-based ransomware syndicate and has stolen more than $120 million since 2019. LockBit operates with the Ransomware-as-a-Service (RaaS) model, where they provide ransomware software to affiliates that carry out attacks on organizations and companies around the world.
LockBit is also known for its multiple extortion tactics, where they not only encrypt the victim's computer system, but also steal sensitive data and threaten to publish it if it is not paid a ransom. LockBit is the most widely used ransomware variant globally in 2022 and is still active today.
SEE ALSO:
One of the biggest victims of LockBit is ICBC, the largest US brokers to be a subsidiary of the Industrial and Commercial Bank of China. On November 9, 2023, LockBit launched a ransomware attack that stopped ICBC operations and disrupted the settlement of more than $9 billion (Rp140 trillion) assets supported by the Treasury securities.
The attack also caused ICBC to lose access to internal email and communications, as well as deliver unfunded securities in favor of trading. LockBit demanded a ransom of US$20 million (Rp312 billion) from ICBC, but it is not known whether ICBC paid or not.
The US and Britain have teamed up with various international law enforcement agencies to pursue LockBit and its affiliates. Britain's National Crime Agency has even managed to take over LockBit's technical infrastructure, including their dark web sites used to store and display data stolen from victims.
The spike in LockBit Ransomware Attacks is not the only ransomware threat that haunts cyberspace. According to a recent report from Chainalysis, a blockchain analysis firm, ransomware payments jumped more than 300% in 2023, hitting a record high of $1.1 billion.
The report also shows that the frequency, scale, and magnitude of ransomware attacks increased significantly in 2023, with various entities, ranging from major criminal syndicates to small and individual groups, engaging in these activities.
Several examples of major ransomware attacks that occurred in 2023 were attacks on Colonial Pipeline, the US's largest oil pipeline company, which caused fuel shortages in several states; attacks on JBS, the world's largest meat producer, which disrupted meat supply chains in the US, Canada, and Australia; and attacks on Kaseya, a network management software provider, affecting more than 1,000 organizations worldwide.
The attacks show how vulnerable critical and business infrastructure is to ransomware threats, as well as how important it is to organizations and companies to improve their cybersecurity and prevent ransomware attacks.
The English, Chinese, Japanese, Arabic, and French versions are automatically generated by the AI. So there may still be inaccuracies in translating, please always see Indonesian as our main language. (system supported by DigitalSiber.id)