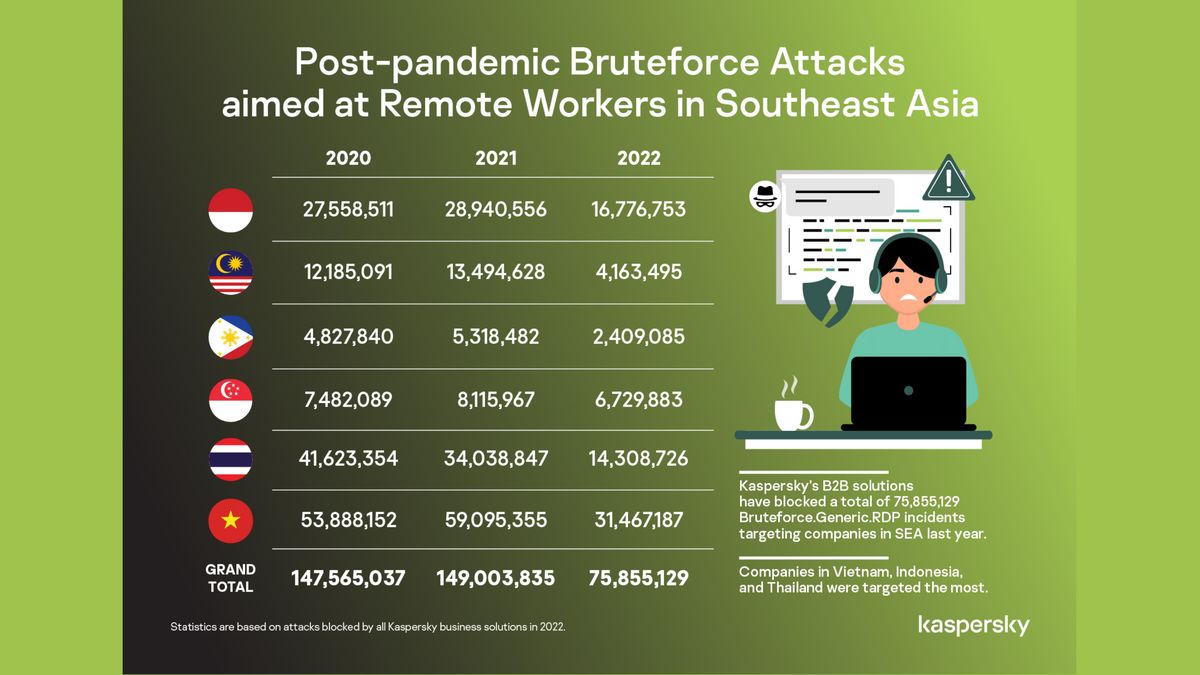
Kaspersky revealed a positive news, in which the global cybersecurity company found a decline in the Bruteforce (49 percent) attack on long-distance workers in Southeast Asia (SEA). However, we must not be complacent.
Remote Desktop Protocol (RDP) is Microsoft's protocol that facilitates users with graphics interfaces to connect to other computers via the network. RDP is widely used by system administrators and non-technical users to remotely control servers and other PCs.
The Bruteforce.Generic.RDP attack usually seeks to find a valid RDP login/code pair by checking all possible passwords until the correct one is found. The attack that successfully allowed the attacker to have long-distance access to the targeted host computer.
Global cybersecurity company telemetry shows Kaspersky's B2B solution has blocked a total of 75,855,129 incidents of Bruteforce.Generic.RDP, from the previous 149,003,835 attacks in 2021, in six Southeast Asian countries.
In terms of last year's Bruteforce share of attacks, companies from Vietnam, Indonesia, and Thailand were the most targeted.
Of the nearly 150 million Bruteforce attacks on companies in Southeast Asia in 2021, last year showed a half decline. That's a good sign at first sight," said Yeo Siang Tiong, General Manager for Southeast Asia at Kaspersky, in a written statement received in Jakarta.
According to Yeo, this is partly influenced by the shift to the return of face-to-face or long-distance activities in a hybrid manner, meaning there are fewer remote workers in the region compared to the peak of the pandemic in 2022 and 2021.
"However, it is too early for businesses to announce the total security of the Bruteforce attack. Looking at the wider threat landscape, our experts are looking at more modern ransomware groups exploiting RDP to gain early access to the companies they are targeting. This is a red flag that security teams must pay attention to," Yeo added.
Kaspersky's recent report revealed the most popular technique for obtaining initial access among ransomware groups, namely utilizing external remote services.
The report also records all ransomware groups using open RDP to gain initial access to the system as it's the easiest vector to get it.
The best practice to protect against attacks related to RDP, is to 'hide it' behind the VPN and configure it appropriately. It is also important to use a strong password.
The English, Chinese, Japanese, Arabic, and French versions are automatically generated by the AI. So there may still be inaccuracies in translating, please always see Indonesian as our main language. (system supported by DigitalSiber.id)